Keamanan siber pdf is the gateway to a safer digital world. In this engaging introduction, we explore the significance of cybersecurity in today’s landscape and how PDFs play a vital role in sharing valuable information. Dive into the world of popular cybersecurity PDFs and uncover the benefits of using them for education and awareness purposes.
Delve deeper into the key concepts and terminologies that make up the foundation of cybersecurity PDFs. Gain insights into their importance for individuals and organizations, and discover commonly used terminologies along the way.
Introduction to Cybersecurity PDFs
Cybersecurity plays a crucial role in today’s digital world. With the increasing reliance on technology and the growing threat of cyberattacks, it is vital to protect sensitive information and ensure the integrity of digital systems. Cybersecurity involves the implementation of measures to prevent unauthorized access, protect against malicious activities, and safeguard data from potential breaches.PDFs
have become a popular format for sharing and disseminating cybersecurity information. Portable Document Format (PDF) offers several advantages, making it an ideal choice for educational materials, research papers, and guidelines related to cybersecurity. PDFs are platform-independent and can be viewed on various devices without any compatibility issues.
They preserve the original formatting, layout, and design of the document, ensuring that the information is presented in a consistent and professional manner.There are numerous cybersecurity PDFs available that address different aspects of online security. These PDFs provide valuable insights and guidance for individuals, businesses, and organizations seeking to enhance their cybersecurity practices.
Radika Karya Utama is an important player in the field of cybersecurity. This article, available here , highlights the significance of legislative and executive authorities in ensuring cyber security. Radika Karya Utama’s contributions in this area are commendable. With their expertise and innovative solutions, they have played a crucial role in protecting individuals and organizations from cyber threats.
Their dedication to safeguarding digital assets is vital in today’s increasingly interconnected world.
Some popular cybersecurity PDFs include guidelines for secure password management, best practices for data protection, strategies for network security, and frameworks for risk assessment and management.Using PDFs for cybersecurity education and awareness offers several benefits. Firstly, they provide a comprehensive and organized way to present information, making it easier for readers to understand complex concepts and follow step-by-step instructions.
Former Indonesian President Susilo Bambang Yudhoyono (SBY) represented the alumni of Akademi Angkatan Bersenjata Republik Indonesia (Akabri) in praying for the success of Prabowo Subianto in leading the nation. The news, which can be found here , highlights SBY’s support for Prabowo, who is currently serving as the country’s leader.
This gesture from SBY and the Akabri alumni demonstrates their confidence in Prabowo’s ability to navigate the challenges and steer the nation towards success.
PDFs can include visual aids, such as diagrams and infographics, to enhance understanding. They can also incorporate interactive elements, such as hyperlinks and bookmarks, to facilitate navigation and access to additional resources.Moreover, PDFs can be easily shared and distributed, allowing cybersecurity professionals to reach a wide audience and promote awareness about potential threats and preventive measures.
PDFs can be downloaded and accessed offline, ensuring that the information remains available even without an internet connection. This accessibility makes PDFs a valuable resource for individuals and organizations seeking to educate themselves or their employees about cybersecurity.In conclusion, cybersecurity PDFs play a vital role in disseminating knowledge and promoting awareness about online security.
They offer a convenient and effective way to share information, provide guidance on best practices, and educate individuals and organizations about the importance of cybersecurity in today’s digital landscape.
Key Concepts and Terminologies in Cybersecurity PDFs: Keamanan Siber Pdf
Cybersecurity is a rapidly evolving field that requires a solid understanding of key concepts and terminologies. In this section, we will explore some of the commonly found concepts in cybersecurity PDFs and discuss their significance for individuals and organizations.
Threat
A threat refers to any potential danger or risk to the security of computer systems, networks, or data. Threats can come in various forms, such as malware, hackers, or unauthorized access attempts. Understanding different types of threats and their characteristics is crucial for developing effective security strategies.
Vulnerability
A vulnerability is a weakness or flaw in a system that can be exploited by attackers to gain unauthorized access or cause damage. Identifying vulnerabilities and addressing them promptly is essential to prevent security breaches. Regular security assessments and patching of software are common practices to mitigate vulnerabilities.
Risk Assessment
Risk assessment involves evaluating the potential risks and their impact on an organization’s assets and operations. It helps in identifying the likelihood of threats exploiting vulnerabilities and provides a basis for prioritizing security measures. Conducting regular risk assessments enables organizations to make informed decisions regarding resource allocation and risk mitigation strategies.
Authentication
Authentication is the process of verifying the identity of a user or system entity. It ensures that only authorized individuals or systems can access resources or perform specific actions. Common authentication methods include passwords, biometrics, and cryptographic keys.
Encryption
Encryption is the process of converting data into a form that is unintelligible to unauthorized users. It ensures the confidentiality and integrity of sensitive information during storage or transmission. Encryption algorithms and keys play a vital role in securing data in various applications, such as email communication and online transactions.
Firewall
A firewall is a network security device that monitors and controls incoming and outgoing network traffic. It acts as a barrier between internal and external networks, preventing unauthorized access and filtering potentially malicious traffic. Firewalls are an essential component of network security infrastructure.
Intrusion Detection System (IDS)
An Intrusion Detection System (IDS) is a security tool that monitors network or system activities for signs of malicious behavior or policy violations. It analyzes network packets, log files, or system events to detect and respond to potential security incidents.
IDS helps organizations in detecting and mitigating attacks in real-time.
Security Incident Response
Security incident response involves a coordinated approach to address and manage security breaches or incidents. It includes steps such as identifying the nature and scope of the incident, containing the impact, mitigating the damage, and conducting forensic analysis to prevent future incidents.
Having a well-defined incident response plan is critical for minimizing the impact of security incidents.
Cybersecurity Best Practices PDFs
Following cybersecurity best practices is of utmost importance for both individuals and organizations. With the increasing frequency and sophistication of cyber threats, implementing best practices can help prevent data breaches, protect sensitive information, and maintain the integrity of systems and networks.There
are different categories of cybersecurity best practices that address various aspects of security. These include:
1. Password Management, Keamanan siber pdf
Effective password management is crucial in safeguarding accounts and preventing unauthorized access. Best practices in this category include:
- Using strong and unique passwords for each account
- Regularly updating passwords
- Enabling multi-factor authentication
2. Software Updates and Patching
Keeping software and applications up to date is essential for addressing vulnerabilities and protecting against known exploits. Best practices in this category involve:
- Regularly installing software updates and patches
- Enabling automatic updates whenever possible
- Using reputable software sources
3. Phishing Awareness
Phishing attacks are one of the most common cybersecurity threats. Best practices in this category focus on educating individuals and organizations to recognize and avoid phishing attempts. These include:
- Being cautious of suspicious emails, links, and attachments
- Verifying the sender’s identity before sharing sensitive information
- Regularly training employees on phishing awareness
4. Data Backup and Recovery
Regularly backing up data is crucial in mitigating the impact of potential data loss or ransomware attacks. Best practices in this category include:
- Creating regular backups of important data
- Storing backups in a secure location
- Testing data recovery processes
Popular Cybersecurity Best Practice PDFs
There are several popular cybersecurity best practice PDFs available that provide detailed guidelines on implementing security measures. Some examples include:
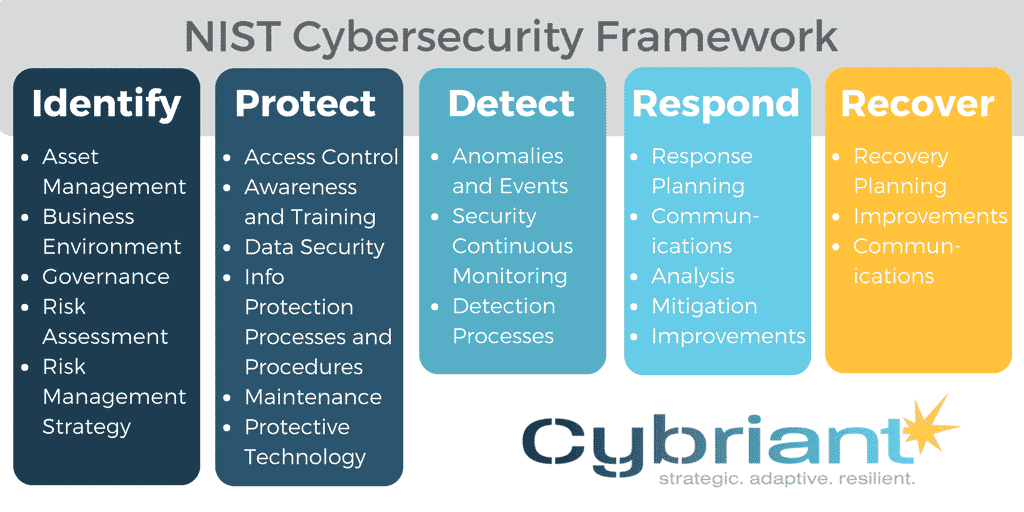
- “NIST Cybersecurity Framework” – This PDF Artikels a comprehensive framework for managing and reducing cybersecurity risks.
- “SANS Top 20 Critical Security Controls” – This PDF lists the top 20 security controls that organizations should implement to protect against cyber threats.
- “OWASP Secure Coding Practices” – This PDF provides guidance on secure coding practices to prevent common vulnerabilities in software development.
PDFs play a significant role in promoting and disseminating cybersecurity best practices. They provide a structured and easily accessible format for sharing detailed information and guidelines. PDFs can be distributed digitally, making them accessible to a wide audience. They can also be printed and used as reference materials or training resources.By
utilizing PDFs, individuals and organizations can effectively communicate and educate others about cybersecurity best practices, ultimately contributing to a more secure digital environment.
Cybersecurity Threats and Mitigation Strategies in PDFs

Cybersecurity threats pose significant risks to both individuals and organizations in today’s digital landscape. Understanding the different types of threats and their potential impact is crucial in developing effective mitigation strategies. PDFs play a vital role in educating and raising awareness about cybersecurity threats and the necessary steps to mitigate them.
Common Cybersecurity Threats
- Malware: Malicious software such as viruses, worms, and ransomware that can compromise systems and steal sensitive information.
- Phishing: Deceptive emails, messages, or websites designed to trick individuals into revealing personal information or login credentials.
- Social Engineering: Manipulative techniques used to exploit human psychology and gain unauthorized access to systems or sensitive data.
- Denial of Service (DoS) Attacks: Overwhelming a network or website with excessive traffic to disrupt its normal functioning.
- Insider Threats: Malicious actions or data breaches caused by individuals within an organization, such as disgruntled employees.
Importance of Understanding Threats and Their Impact
Having a comprehensive understanding of different cybersecurity threats is crucial for individuals and organizations to protect themselves effectively. By understanding the potential impact of these threats, measures can be put in place to prevent or minimize damage.
Examples of Cybersecurity Threat PDFs and Mitigation Strategies
Cybersecurity threat PDFs often provide valuable information and guidance on how to mitigate specific threats. Examples include:
- “Protecting Yourself from Phishing Attacks”: This PDF educates individuals about common phishing techniques and provides practical tips on how to identify and avoid falling victim to phishing attempts.
- “Securing Your Network from DoS Attacks”: This PDF Artikels different mitigation strategies, such as implementing traffic filtering, load balancing, and using intrusion detection systems, to protect networks from DoS attacks.
- “Best Practices for Employee Awareness”: This PDF focuses on raising awareness among employees about social engineering tactics and provides guidelines on how to identify and respond to potential threats.
Role of PDFs in Cybersecurity Education and Awareness
PDFs serve as effective tools for educating individuals and organizations about cybersecurity threats and mitigation strategies. They provide a structured format that can be easily disseminated and accessed by a wide audience. PDFs can be shared through various channels, such as websites, email attachments, and online training platforms, ensuring that important cybersecurity information reaches the intended recipients.
Outcome Summary

As we conclude this discussion, let’s reflect on the power of keamanan siber pdf in promoting cybersecurity best practices. Explore the different categories of best practices and unravel the significance of PDFs in disseminating this crucial information. Stay informed, stay secure, and take charge of your digital safety.
FAQ Overview
What are the benefits of using keamanan siber pdf for cybersecurity education?
Keamanan siber pdf offers a user-friendly and accessible format for sharing cybersecurity knowledge. It allows for easy distribution, offline access, and preservation of valuable information, making it an effective tool for educating individuals and organizations.
How can keamanan siber pdf contribute to cybersecurity awareness?
By utilizing keamanan siber pdf, cybersecurity awareness materials can reach a wider audience. PDFs can be easily shared through various platforms, making it convenient for individuals to access and digest important information about cybersecurity threats and best practices.